Kubernetes Dashboard Vulnerability . Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. It is divided into the following categories: There are three key elements of kubernetes vulnerability scanning: This cheat sheet provides a starting point for securing a kubernetes cluster. Receive alerts for kubernetes updates. In this blog post we’ll explore some. Remediating vulnerabilities in kubernetes itself, container. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by.
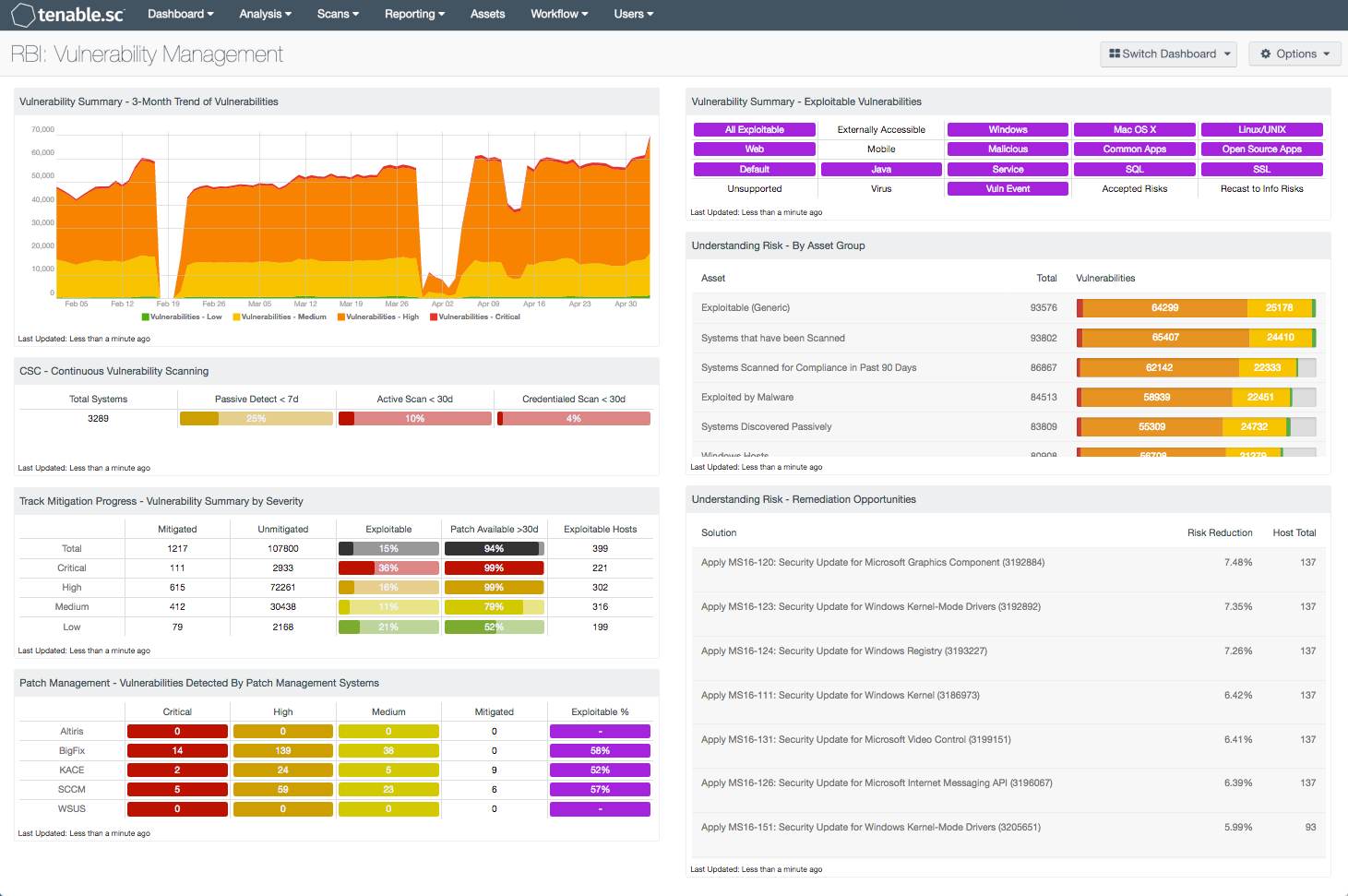
from www.tenable.com
This cheat sheet provides a starting point for securing a kubernetes cluster. In this blog post we’ll explore some. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. Receive alerts for kubernetes updates. Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. Remediating vulnerabilities in kubernetes itself, container. It is divided into the following categories: There are three key elements of kubernetes vulnerability scanning:
RBI Vulnerability Management SC Dashboard Tenable®
Kubernetes Dashboard Vulnerability There are three key elements of kubernetes vulnerability scanning: Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. Receive alerts for kubernetes updates. There are three key elements of kubernetes vulnerability scanning: Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. It is divided into the following categories: In this blog post we’ll explore some. This cheat sheet provides a starting point for securing a kubernetes cluster. Remediating vulnerabilities in kubernetes itself, container.
From blog.opsramp.com
Close the Visibility Gap for Modern Cloud Native Services with OpsRamp Kubernetes Dashboard Vulnerability This cheat sheet provides a starting point for securing a kubernetes cluster. Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. In this blog post we’ll explore some. It is divided into the following categories: Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. There are three key elements. Kubernetes Dashboard Vulnerability.
From www.altoros.com
Improving Security for Deployments at Scale Altoros Kubernetes Dashboard Vulnerability Receive alerts for kubernetes updates. It is divided into the following categories: In this blog post we’ll explore some. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. There are three key elements of kubernetes vulnerability scanning: Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. This cheat sheet. Kubernetes Dashboard Vulnerability.
From www.dynatrace.com
Get deep observability with the new cloud application view Kubernetes Dashboard Vulnerability This cheat sheet provides a starting point for securing a kubernetes cluster. Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. Receive alerts for kubernetes updates. Remediating vulnerabilities in kubernetes itself, container. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. It is divided into the following categories:. Kubernetes Dashboard Vulnerability.
From medium.com
A Story of Debugging an Unexpectedly Slow SQL Query Powering our Kubernetes Dashboard Vulnerability Receive alerts for kubernetes updates. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. This cheat sheet provides a starting point for securing a kubernetes cluster. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. There are three key elements of kubernetes vulnerability scanning: In this blog post we’ll. Kubernetes Dashboard Vulnerability.
From s4applications.uk
Vulnerability Management Programme And Dashboards S4 Applications Kubernetes Dashboard Vulnerability In this blog post we’ll explore some. Receive alerts for kubernetes updates. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. There are three key elements of kubernetes vulnerability scanning: This cheat sheet provides a starting point for securing a kubernetes cluster. Remediating vulnerabilities in kubernetes itself, container. It is divided into the following. Kubernetes Dashboard Vulnerability.
From elastisys.io
Vulnerability Dashboard Elastisys Compliant Kubernetes Dashboard Vulnerability Receive alerts for kubernetes updates. It is divided into the following categories: Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. Remediating vulnerabilities in kubernetes itself, container. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. This cheat sheet provides a starting point for securing a kubernetes cluster. In. Kubernetes Dashboard Vulnerability.
From www.docs.secpod.com
How to remediate vulnerabilities from vulnerability management Kubernetes Dashboard Vulnerability Remediating vulnerabilities in kubernetes itself, container. This cheat sheet provides a starting point for securing a kubernetes cluster. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. In this blog post we’ll explore some. It is divided into the following categories: There are three key elements of kubernetes vulnerability scanning: Receive alerts for kubernetes. Kubernetes Dashboard Vulnerability.
From db-excel.com
Vulnerability Tracking Spreadsheet for Vulnerability Management Metrics Kubernetes Dashboard Vulnerability Receive alerts for kubernetes updates. It is divided into the following categories: There are three key elements of kubernetes vulnerability scanning: Remediating vulnerabilities in kubernetes itself, container. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. In this blog post we’ll explore some. Kubernetes v1.27 [beta] this is a community maintained list of official. Kubernetes Dashboard Vulnerability.
From www.tenable.com
RBI Vulnerability Management SC Dashboard Tenable® Kubernetes Dashboard Vulnerability Remediating vulnerabilities in kubernetes itself, container. In this blog post we’ll explore some. This cheat sheet provides a starting point for securing a kubernetes cluster. It is divided into the following categories: Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced. Kubernetes Dashboard Vulnerability.
From www.sumologic.com
Understanding the Impact of the Security Flaw and Why Kubernetes Dashboard Vulnerability Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. In this blog post we’ll explore some. It is divided into the following categories: Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. This cheat sheet provides a starting point for securing a kubernetes cluster. There are three key. Kubernetes Dashboard Vulnerability.
From www.secpod.com
The Vulnerability Management Dashboard Every CISO Needs! Kubernetes Dashboard Vulnerability Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. It is divided into the following categories: In this blog post we’ll explore some. This cheat sheet provides a starting point for securing a kubernetes cluster. Remediating vulnerabilities in kubernetes itself,. Kubernetes Dashboard Vulnerability.
From www.practical-devsecops.com
What is Vulnerability Scanning? Kubernetes Dashboard Vulnerability Receive alerts for kubernetes updates. There are three key elements of kubernetes vulnerability scanning: In this blog post we’ll explore some. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. This cheat sheet provides a starting point for securing a kubernetes cluster. Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service. Kubernetes Dashboard Vulnerability.
From threatconnect.com
Vulnerability Prioritization Technology ThreatConnect Kubernetes Dashboard Vulnerability Receive alerts for kubernetes updates. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. In this blog post we’ll explore some. Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. Remediating vulnerabilities in kubernetes itself, container. It is divided into the following categories: This cheat sheet provides a starting. Kubernetes Dashboard Vulnerability.
From b.hatena.ne.jp
[B! A 3step guide to troubleshooting and visualizing Kubernetes Dashboard Vulnerability There are three key elements of kubernetes vulnerability scanning: It is divided into the following categories: This cheat sheet provides a starting point for securing a kubernetes cluster. Remediating vulnerabilities in kubernetes itself, container. Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. Our open source starboard project integrates vulnerability scanning (and other security checks). Kubernetes Dashboard Vulnerability.
From www.01net.it
Primi passi con onpremise e in cloud Kubernetes Dashboard Vulnerability Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. Remediating vulnerabilities in kubernetes itself, container. It is divided into the following categories: This cheat sheet provides a starting point for securing a kubernetes cluster. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. In this blog post we’ll explore. Kubernetes Dashboard Vulnerability.
From sysdig.com
Dashboard CVE201818264 Overview Sysdig Kubernetes Dashboard Vulnerability Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. This cheat sheet provides a starting point for securing a kubernetes cluster. Receive alerts for kubernetes updates. Our open source starboard project integrates vulnerability scanning (and other security checks) into the kubernetes. In this blog post we’ll explore some. It is divided into the following. Kubernetes Dashboard Vulnerability.
From ikarus.sg
My Dashboard and How To Deploy Yours Kubernetes Dashboard Vulnerability It is divided into the following categories: Kubernetes dashboard before 1.10.1 allows attackers to bypass authentication and use dashboard's service account for. In this blog post we’ll explore some. There are three key elements of kubernetes vulnerability scanning: Remediating vulnerabilities in kubernetes itself, container. Receive alerts for kubernetes updates. Kubernetes v1.27 [beta] this is a community maintained list of official. Kubernetes Dashboard Vulnerability.
From ikarus.sg
My Dashboard and How To Deploy Yours Kubernetes Dashboard Vulnerability Kubernetes v1.27 [beta] this is a community maintained list of official cves announced by. This cheat sheet provides a starting point for securing a kubernetes cluster. It is divided into the following categories: In this blog post we’ll explore some. Remediating vulnerabilities in kubernetes itself, container. There are three key elements of kubernetes vulnerability scanning: Our open source starboard project. Kubernetes Dashboard Vulnerability.